|
|
|
| This article is available in: English Castellano Deutsch Francais Portugues Russian Turkce |
![[Photo of the Author]](../../common/images/Georges-Tarbouriech.jpg)
by Georges Tarbouriech <georges.t(at)linuxfocus.org> About the author: Georges is a long time Unix user. He thinks computer security is
one of the main challenges of this century. Content: |
![[illustration]](../../common/images/article217/illustration217.png)
Abstract:
Nessus is a free security scanner available from http://www.nessus.org. The project was started and is maintained by Renaud Deraison. The stable version at the time of this writing is 1.09 and the experimental one is 1.14. The software is released under GPL (Gnu Public License) and many people contribute to the project, especially for plugins... while some other people benefit from nessus work without even mentioning the name (more on this at the end of the article). Nessus works on many Unix flavors as a client and a server, and on Win32 as a client. Let's have a look at this great tool.
Going to http://www.nessus.org, you can get this great
piece of software. Since nessus is also available as a client for Win32, we
obviously will consider the Posix version in this article.
To use nessus, you need at least nmap and Gtk (Gimp Toolkit). Links to those tools
are provided from nessus' website. However, since you can use nessus from the
command line, Gtk is not mandatory.
You can get nessus in three different
ways : the good, the bad and the ugly.
The good way is the standard one, that
is, you download the archives from the ftp site closest you. You have four
archives : nessus libraries, nasl libraries, nessus core and nessus plugins.
Once unpacked, you build and install them as usual : ./configure, make, make
install, for all the archives. If you have a previous version of
nessus installed on your machine, you'll have to remove it. To do this,
nessus provides an uninstall script to use after the first
"./configure" in the nessus libraries package. Run this script before
typing "make". Do the same for each provided package (except running the
uninstall script) and you're done.
The bad way, is to run a downloadable script called
nessus-installer.sh. Then typing "sh nessus-installer.sh" will auto-install
the package. The four packages don't need to be installed separately. It's now just one stand-alone package.
The ugly way : as long as you have lynx installed on your machine and you're
connected to the Internet, just type "lynx -source http://install.nessus.org
| sh" and that's it. You must NOT be root to do this.
Obviously, we recommend the "good" way... well, if you download
nessus, we suppose security matters to you ! Since we're talking about
security, don't forget to check the MD5 checksum.
Nessus comes with different utilities (nasl, a scripting language,
nessus-adduser, nessus-build...). Each of these utilities has its own man
page for the client and the server. More documentation is available
within the distribution (README, INSTALL...) or on the nessus website.
To make things easier to understand, we'll show examples with the nessus X11 version, the one that uses Gtk.
The nessusd server
To start nessus, you obviously need to run the server daemon, nessusd. When
launching the daemon for the first time you'll have to create a username and
password by using the nessus-adduser command.
If the nessus libraries package has been compiled with the
"--enable-cipher" option (highly recommended, not to say mandatory !),
nessus generates a private key.
This key can be protected with a passphrase. The server has many options
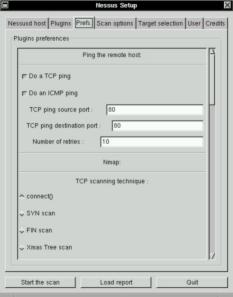
available and you'll find them all in the nessusd man page.
From there you can create the user database and the corresponding rules. That determines
who may to run the server daemon and what you will allow her to scan (a
machine, a network...). The rules are of the form "accept" or "deny"
followed by a network IP address with its netmask.
For example : accept 192.168.1.0/24, allows the user to test the whole
192.168.1 network.
It's also possible to define one single user with no rules at all. If you
wish to allow various users to run nessusd, you'll have to be very careful
about what you allow them to do. You can't let everybody do everything
on your network, can you ?
Last, nessusd relies on a configuration file (usually) found in
/usr/local/etc/nessus/nessusd.conf. You can change this file by hand - as
soon as you know what you're doing.
After configuring and starting the demon, you can start the nessus client to connect to the nessusd server.
One way to run the client is to type "nessus &" in a shell. This opens the nessus
setup window after asking for the above mentioned passphrase. This window provides you with seven tabs.
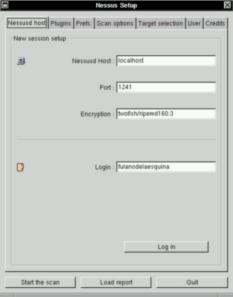
The first tab is called "nessusd host". From it you can connect to the
nessusd host clicking on the "Log in" button. Of course, this assumes you're
allowed to connect as this user, in other words, that your username exists
in the user database.
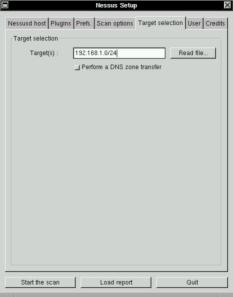
When you start the scan, nessus opens a window displaying the scan status.
For example, let's say you are testing a whole network, called
192.168.1.0/24. Eight machines (hosts) will be displayed at once,
showing which plugin is used for which machine and a progress gauge.
It looks like this:
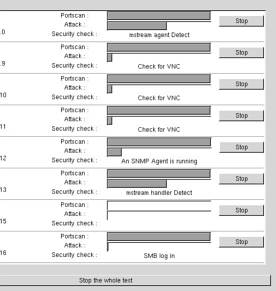
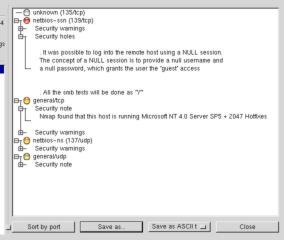
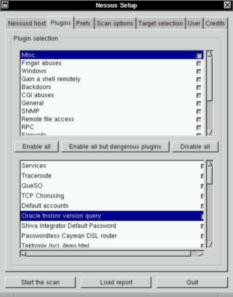
Plugins are the "heart" of nessus. They are security tests - that is test programs to
discover a given vulnerability. NASL (Nessus Attack Scripting Language) is the
recommended language to write security tests. You'll find a lot about NASL going
to this URL : http://www.nessus.org/doc/nasl.html.
Accordingly, if you
want to contribute to the nessus project writing plugins, this is where
you'll find the right information. At the time of this writing, there are
756 plugins in nessus' database !
There are almost 20 plugin families : backdoors, denial of service, gain
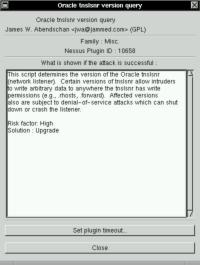
root remotely... As already mentioned, each plugin reports information. It
tells you what's wrong and what you should do to correct the problem.
We can't talk about plugins without mentioning CVE (Common Vulnerabilities
and Exposures). It's a huge information database available from
http://cve.mitre.org. There you'll find
all the details about known security risks. Another great place to share knowledge.
This website is the absolute reference that you must visit.
Of course, there's a lot to say about nessus plugins, but a book wouldn't be
enough. A good way to understand how they work and how they are written is to
read them from your /usr/local/lib/nessus/plugins directory.
Thanks again to Renaud Deraison and contributors for doing such a great job.
Even if this title sounds like Monty Python, unfortunately there is no humor
in it. The three or four people reading my articles know about my usual
off-topic sentences : this time, it's a whole section ! Is it really off-topic,
that's another story. Let's go.
Since I'm quite interested in computer security, I often visit the dedicated
websites. Sometimes to learn about new vulnerabilities or to discover new
security tools. Incidentally, I found a few products based on an
online scanning service. In fact they call themselves (at least for
now) ASP (Application Service Provider). If you go a bit further, you quickly
discover that the engine behind the service is nessus. So far, so good.
However, when trying to find the explicit information
you can't see the word "nessus". That's where I'm hurt !
Many people working for the free software community do this work for free,
not for a living. The only payment they get is called : credit. Nessus
is released under the GPL. That is, everyone can use the product, modify the source code,
adapt it... as long as they mention the original author(s). Of course, the
license says much more than this. If you don't
know the GPL, have a look there.
To me, this looks like a theft. I mean, I don't even need a license to credit
other people's work. I have very much respect for those people working for free
(almost always) and sharing with a community. They deserve recognition from
that community. This is especially true when people try to make money from somebody else's work.
You can call that respect, recognition, it doesn't matter. The fact is, those
words seem to have lost their meaning. Sure, we could say the GPL is the cause
of such behavior. With ASP, you're not considered to be selling the software.
Depending on the country, the GPL may have no legal value.
A solution could be that the users of such ASPs request the name of the scanning engine
doing the real work. The answer given will at least show if the people
providing the service are "honest". If they don't answer or if they say they
"invented" that engine (which you identified as nessus), just don't use it !
Install nessus instead (the true one), it'll be more secure anyway.
But again, do we need a license to say "thank you" to people having done a really
big and great job ? And, by the way, Renaud Deraison doesn't want to change
nessus license : nessus will stay under GPL.
Sorry for that long digression, but I believe it had to be said.
Despite the last section, what to remember from this article is that nessus provides a high quality
standard. It's quite an impressive software. Used in conjunction with
nmap, it becomes a must have whenever security is a concern. It is a very responsible
tool, improving every day. Thanks to Renaud and friends for their constant
updates to plugins.
Today, a sysadmin can't work without nessus and nmap. These tools
find vulnerabilities you thought you solved. This is true for most of the
OSes found on your network. And when you know that some OSes are like sieves,
nessus lets you relax a bit.
Even more, nessus can help you understand the way a network (or a machine)
can be compromised.
If you read the reports provided carefully, take them into
account and make the right corrections, you'll improve the security of
that network (or machine) considerably. Again, I said "improve" : your network won't be 100%
secure just because you run nessus. The road to security is a very long one and we
are far from the end of it.
Once more, thanks to the free software community for the great work it does
about security.
Concerning those nice people trying to make money from the work of this free
software community members, I'd like to add something. Saying "thanks" is not a badge of shame.
Being honest is not that awful, is it ? If this kind of behavior grows,
the risk is either the end of the community or a big change in
licensing (and probably more and more patents !). In either case, you'll be on your own and things will become much
harder for you. And unfortunately, we won't be able to use free software anymore. This
doesn't mean you'll be able to sell yours. Think it over !
Aren't we living in a great time ?
|
|
Webpages maintained by the LinuxFocus Editor team
© Georges Tarbouriech, FDL LinuxFocus.org Click here to report a fault or send a comment to LinuxFocus |
Translation information:
|
2001-12-27, generated by lfparser version 2.23