| This article is available in: English Castellano Deutsch Francais Nederlands Turkce |
![[Photo of the Author]](../../common/images/Atif-Ghaffar.jpg)
by Atif Ghaffar About the author:
Atif is a chameleon. He changes his roles, from System Administrator, to programmer, to teacher, to project manager, to whatever is required to get the job done.
Content:
|

Abstract:
In this Article we will explore LDAP and its implementations using our favourite OS Linux.
There is a lot of literature about LDAP out there so I wont repeat it again here, neither will I talk about advanced LDAP terms, schemas, v2 versus v3 difference etc. In fact i do not know much about them. Instead I will try to explain in very simple words about what LDAP is, what its benefits and how we can use it.
I am not an LDAP expert. In fact I am an LDAP beginner. I will basically just write here what I do with LDAP and how. I will try not to confuse you like I was for a very long time.
Question: If you are a beginner, why write an article about it?
Recently I needed help on a project from a colleague. The base of the project was LDAP. He could help me with Perl, mail servers etc but did not know anything about LDAP, in fact each time he wanted to get into LDAP, it got more and more confusing.
Since being comfortable with LDAP was the minimum requirement for the project, I gave him a crash course about LDAP in half an hour and it became suddenly all clear. The concepts were so easy, it was all in front, but just needed a bit of focus or some funny examples.
I will try to do the same in this article.
You can find many urls in the reference section to learn more about LDAP.
LDAP stands for (Lightweight Directory Access Protocol) and is a directory service, very similar to the directories on the file system that we are used to and also similar to the telephone book that we use to lookup phone numbers, and also network directory services such as SUN's NIS (Network Information Service), DNS (Domain Name Service) , and also to the tree that you see in your ( or your neighbor's) garden etc.
LDAP is a specialized database. It is very important to remember that LDAP is not just another database. LDAP is optimized to make lookups (read data). Reads in LDAP are performed much more often than writes.
What do all these services have in common?
The all return some information when queried about a criteria.
Examples.
File system directory
ls /etc
This will return all files and subdirectories in the folder /etc
ls /etc/p*
This will return all files and subdirectories that begin with p
find /usr/local/apache -name index.html
This will search the file system for a file/directory called index.html , starting from the base "/usr/local/apache"
NIS directory
ypcat passwd
This will return the username, password, userid etc from the NIS database
ypmatch atif passwd
This will return entries from the password for the user atif
DNS directory
nslookup www.linuxfocus.org
This will return the ip address for the entry www.linuxfocus.org from the DNS database
nslookup -type MX linuxfocus.org
This will return only MX information from the dns database where hostname matches linuxfocus.org
LDAP directory
(we will look into them in detail below)
ldapsearch uid=aghaffar
This will return all public information about the user aghaffar
Similar to unix find / -uid aghaffar command
ldapsearch uid=aghaffar mail
This will only return mail of user aghaffar
In each directory service we mentioned above there is always a starting point from where one can start browsing or searching. This starting point is often called "root".
This is similar to the root in the tree.
Each tree has a root, then some branches and more branches and leaves and flowers etc.
drwxr-xr-x 29 root root 749 Jun 17 23:45 /usr
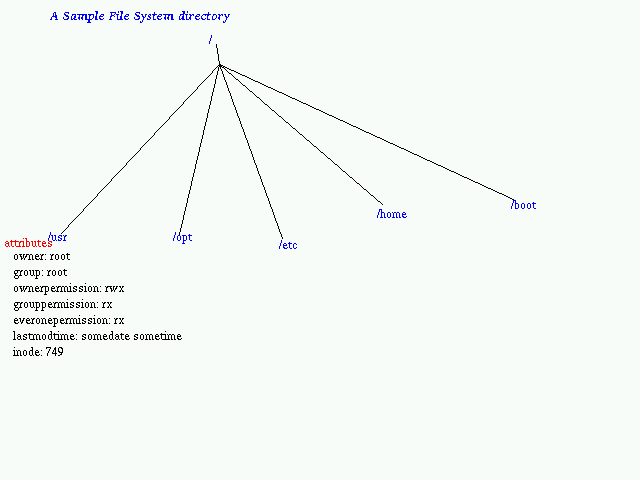
Now a diagram for an LDAP Directory
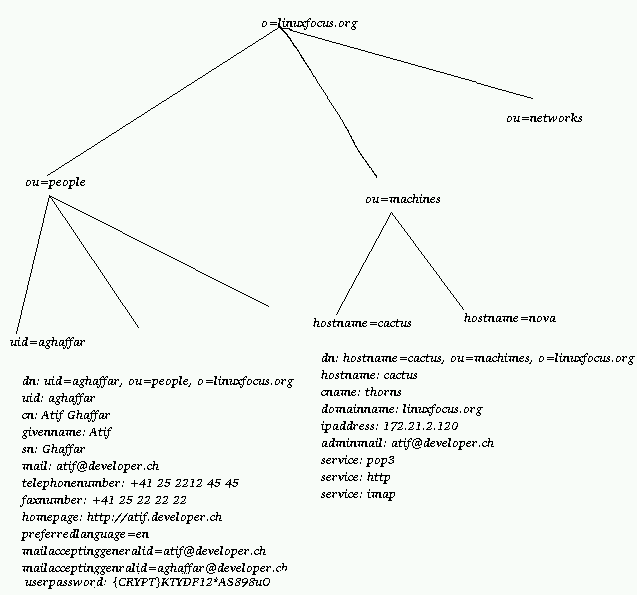
We will talk about this diagram later.
Unlike the natural tree, each branch of the filesystem/LDAP/Phonebook Directory has at least one unique attribute , which helps us tell difference of one from the other.
On file systems this unique attribute is the filename along with the path. for example
/etc/passwd
Here The filename passwd has to be unique within this path. Of course we can have /usr/passwd , /opt/passwd which are all unique by their fully qualified filename.
Similarly the DNS system has FQDN (Fully Qualified Domain Name) which is a unique entry (of coarse you can assign a lot of ip to the same FQDN smart boy!).
In LDAP the fully qualified name of an entry is called "dn" or Distinguished name. This name is always unique in a directory.
for example my dn is "uid=aghaffar, ou=People, o=developer.ch"
It is not possible to have another entry with the same dn, but surely we can have a dn such as "uid=aghaffar, ou=Administrators, o=developer.ch"
This represents the example of file system entries /etc/passwd and /usr/passwd
We have a unique attribute called uid in the tree "ou=Administrators, o=developer.ch" and we have a unique attribute called uid in the tree "ou=People, o=developer.ch".
They do not clash.
There are many LDAP servers available on the market today and most will work on Linux.
For this article we will use openLDAP.
Why I chose openLDAP? Why should you choose openLDAP?
In this section we will setup an LDAP server step by step.
Steps to take:
As mentioned before, either download the sources from www.openldap.com and install it according to the documentation or install a pre-compiled package(installing of the packages or a howto on compiling applications is out of the scope of this Article)
For this example, I will build and LDAP directory for linuxfocus.org.
You can change names etc to reflect your site.
to setup the main server to have to edit the files slapd.conf and ldap.conf in your favorite editor.
On my servers this file is in /etc/openldap. Yours could be in /usr/local/etc/openldap or else where depending on your Linux Distribution or compile time configuration if you build openldap yourself.
######### /etc/openldap/slapd.conf ################################### # the following are defined by default in my suse 6.4 linux distribution # We will talk more about them in part II or part III of this article # Perhaps by then I will know what they mean :) include /etc/openldap/slapd.at.conf include /etc/openldap/slapd.oc.conf schemacheck off pidfile /var/run/slapd.pid argsfile /var/run/slapd.args ####################################################################### # ldbm database definitions ####################################################################### # this defined the kind of database to use. keep the default ldbm database ldbm # suffix or directory root. This is the top node in your LDAP directory suffix "o=linuxfocus.org" # this is where the ldap dbs will be kept directory /var/lib/ldap # the distinguished name of the directory manager rootdn "cn=Manager, o=linuxfocus.org" # its bad idea to keep the ldap manager password in clear text but we # will use it in the beinning to get used to LDAP rootpw secret # Thats all. for now.Edit your /etc/openldap/ldap.conf
##########/etc/openldap/ldap.conf######### # # LDAP Defaults # # See ldap.conf(5) for details # This file should be world readable. # this defines the ldapserver. you can use hostname or ip address host 127.0.0.1 # this is the directory root we want to use to start searching from. # we will use the top node in our configuration # it need not be the top level node in the directory, for example # we can use base = ou=users, o=linuxfocus.ch # if we do that then all our searched will start from that branch of the tree base o=linuxfocus.org # thats allNow start the ldap server.
At this point you have an ldap server running, ready to be filled up with information.
The standard way to fill information in the ldap server is to create an LDIF (LDAP Directory Interchange Format)* file.
You can read man ldif to find more information about ldif.
Very simply, ldif is the textual representation for ldap entries. These entries are human readable and interchangeable between two different LDAP servers running from different vendors, using different database back-ends or running on different operating systems.
* Yes Yet another format. I wonder why XML is not used instead of LDIF
So without further ado lets create this ldif file.
Some things to remember.
dn: o=linuxfocus.org
o: linuxfocus.org
objectclass: top
objectclass: organization
dn: ou=editors, o=linuxfocus.org
ou: editors
objectclass: organizationalUnit
dn: uid=aghaffar, ou=editors, o=linuxfocus.org
uid: aghafar
cn: Atif Ghaffar
sn: Ghaffar
givenname: Atif
objectclass: person
userpassword: {CRYPT}yIvSBWSuLs2N2
mailacceptinggeneralid: aghaffar@linuxfocus.org
ou: editors
dn: uid=mkempe, ou=editors, o=linuxfocus.org
uid: mkempe
cn: Magnus Kempe
sn: Kempe
givenname: Magnus
objectclass: person
userpassword: clearpass
mailacceptinggeneralid: mkempe@linuxfocus.org
maildrop: mkempe@developer.ch
preferredlanguage: fr
ou: editors
So now we have to add this information in the ldap directory.
Use the command line program called ldapadd
ldapadd -D "cn=Manager, o=linuxfocus.org" -w secret < linuxfocus.org.ldif
This command will use "cn=Manager, o=linuxfocus.org" as the manager's dn(distinguish name) and secret as password and read information from the file linuxfocus.org.ldif and insert it into the ldap directory.
If every thing went all right you are now ready to make queries on your ldap directory, or if it didn't went all right then you are probably ready to flood my mailbox ;)
For my mail server's sake I hope that everything went all right.
Before we continue, lets examine this ldif file line by line.
Lets find all data about user mkempe
ldapsearch uid=mkempe
Lets find the dn for all editors
ldapsearch '(&(objectclass=person)(ou=editors))' dn
For more examples , please read man pages for ldapsearch
LDAP is an open standard. Most new applications that you will use will be able to lookup to ldap database for informations.
Even Windows 2000 uses LDAP for its directory services.
Centralizing all information in one place has enormous benefits, Single point of administration, less error prone, less duplicate data everywhere and the hassle to backing it up.
I can be a complete dork from Compaq and try to sell you LDAP by saying that you can use it as a "contacts manager". But I do not work for Compaq. So I will try to give you some more interesting use of LDAP.
SINGLE SOURCE OF SIGN-ON
User accounts in a central place.
You may want to use an ldap tree to manage your users, their passwords and much more information than you can store in the flat /etc/passwd file. This information can be used for Microsoft Windows / Unix /Mac users.
Idea You may optionally tweak /etc/pam.d/login etc so that authentication is actually done from LDAP information instead of shadow file or nis etc.
Idea You may write a small web interface for users to change their unix password without loggin in the system since the password information is in LDAP and not on the system. You will need to use pam_ldap for this. See resources for url for pam_ldap.
NOTE
Single source of sign-on != single sign-on.
A lot of LDAP vendors try to sell by saying if you implement LDAP you can have a single sign-on solution.
Its only half true. Single Sign on is totally a different animal and a big buzz word among IT Managers these days.
Single sign on example is:
Idea You may want to give users email account on your servers but don't want to create unix accounts. No problem. I am using a combination of LDAP+Postfix MailServer+ Cyrus IMAP/POP Server to manage thousands of users and none of them have a system account.
Idea You may want to centralize preferences for different applications. For example, Netscape preferences, bookmarks etc can be stored in LDAP, and the user can move from one machine to another, receiving his/her preferences from the LDAP server. The user may move from Windows NT Netscape to Linux/Solaris/Macintosh Netscape and still can use the same information. (Sorry Microsoft... I know thats too bad for you)
Scenario
I hate to fill out my informations again and again both at the web and on paper. I don't know why people want to know again and again my age, date of birth, address in government offices when I have already given it to them once. In my last company, we had to setup enormous forms for Help-Desk which were basically 75% the same. (Firstname, Lastname, Title, PostBox, Floor, ManagerName, Department). Instead of pissing off your users and risk being beaten up one dark night by strangers who look very familiar, you may just want to ask your users only the necessary information. For example, ask them for their userid and get the rest of the information from LDAP, then ask them just the missing part.
Idea
For example if my phone is not working, the only new information I have for you is "my phone is not working".
A user would be so much less pissed off with the intranet if :
I hope that with this article, I could help you in some way or feed your hungry brain with some 10011001001001.
You see, you don't have to be an expert to share your knowledge with the community. Neither do you have to be a professor or a teacher to write tutorials. Every little information can help users.
Personally, I find it easy to learn if I try to teach someone about what I already know. You may want to try this technique.
Fortunately I see these days a lot of people talking about Linux, I see a lot of them trying it out too, some give up immediately while some give it a chance for a while. These users may have absolutely no experience of unix commands and concept, while some of them maybe stuck with one problem for a while
If you have faced these problems freshly, then you can be the best teacher for the this batch,
If you don't think that you have any material to write about and still want to help the Linux community, you may want to volunteer to translate these articles in your language.
|
|
Webpages maintained by the LinuxFocus Editor team
© Atif Ghaffar, FDL LinuxFocus.org Click here to report a fault or send a comment to LinuxFocus |
2001-01-27, generated by lfparser version 2.8