25.8. Configure RSA private keys secrets
Recall that currently with FreeSWAN software there are two kinds of secrets:
preshared secrets
RSA private keys.
You need to create a separate RSA key for *each* gateway. Each one gets its private key in its own ipsec.secrets file, and the public keys go in leftrsasigkey and rightrsasigkey parameters in the conn description of ipsec.conf file, which goes to both.
Create a separate RSA key for *each* gateway:
On the first gateway i.e. deep, use the following commands:
[root@deep] /# cd / [root@deep] /# ipsec rsasigkey --verbose 1024 > deep-keys
computing primes and modulus... getting 64 random bytes from /dev/random looking for a prime starting there found it after 30 tries getting 64 random bytes from /dev/random looking for a prime starting there found it after 230 tries swapping primes so p is the larger computing (p-1)*(q-1)... computing d... computing exp1, exp1, coeff... output...
On the second gateway i.e. mail, use the following commands:
[root@mail /]# cd / [root@mail /]# ipsec rsasigkey --verbose 1024 > mail-keys
The rsasigkey utility generates an RSA public and private key pair of a 1024-bit signature, and puts it in the file deep-keys. mail-keys for the second command on the second gateway. The private key can be inserted verbatim into the ipsec.secrets file, and the public key into the ipsec.conf file.computing primes and modulus... getting 64 random bytes from /dev/random looking for a prime starting there found it after 30 tries getting 64 random bytes from /dev/random looking for a prime starting there found it after 230 tries swapping primes so p is the larger computing (p-1)*(q-1)... computing d... computing exp1, exp1, coeff... output...
 :
The rsasigkey utility may pause for a few seconds if not enough entropy is available immediately. You may want to give it some bogus activity such as random mouse movements. The temporary RSA.
deep-keys and mail-keys files should be deleted as soon as you are done with it. Don't forget to delete the deep-keys and mail-keys RSA files.
:
The rsasigkey utility may pause for a few seconds if not enough entropy is available immediately. You may want to give it some bogus activity such as random mouse movements. The temporary RSA.
deep-keys and mail-keys files should be deleted as soon as you are done with it. Don't forget to delete the deep-keys and mail-keys RSA files.
Modify your /etc/ipsec.conf files to use RSA public keys in *each* gateway:
Edit you original ipsec.conf file, vi /etc/ipsec.conf and add the following parameters related to RSA in the conn desciption of your ipsec.conf file on both gateway:
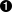
- This parameter specifies how the two security gateways should authenticate each other. The default value is secret for shared secrets. We must specify rsasig for RSA since we have decided to use RSA digital signatures.
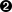
- This parameter specifies the left participant's public key for RSA signature authentication. In our example, left is 208.164.186.1, and represents deep.openna.com, so we must put the RSA public key for deep on this line.
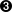
- This parameter specifies the right participant's public key for RSA signature authentication. In our example, right is 208.164.186.2, and represents mail.openna.com, so we must put the RSA public key of mail on this line.
You can retrieve the public key of deep in the RSA key file called deep-keys, and the public key of mail in the RSA key file named mail-keys, that we have created in above step. These files will look like this: RSA keys for gateway deep (deep-keys):
[root@deep] /# cd / [root@deep] /# vi deep-keys
# 1024 bits, Fri Feb 4 05:05:19 2000 # for signatures only, UNSAFE FOR ENCRYPTION #pubkey=0x010395daee1be05f3038ae529ef2668afd79f5ff1b16203c9ceaef801cea9cb74bcfb51a6ecc08890d3eb4b5470c0fc35465c8ba2ce9d1145ff07b5427e04cf4a38ef98a7f29edcb4d7689f2da7a69199e4318b4c8d0ea25d33e4f084186a2a54f4b4cec12cca1a5deac3b19d561c16a76bab772888f1fd71aa08f08502a141b611f Modulus: 0x95daee1be05f3038ae529ef2668afd79f5ff1b16203c9ceaef801cea9cb74bcfb51a6ecc08890d3eb4b5470c0fc35465c8ba2ce9d1145ff07b5427e04cf4a38ef98a7f29edcb4d7689f2da7a69199e4318b4c8d0ea25d33e4f084186a2a54f4b4cec12cca1a5deac3b19d561c16a76bab772888f1fd71aa08f08502a141b611f PublicExponent: 0x03 # everything after this point is secret PrivateExponent: 0x63e74967eaea2025c98c69f6ef0753a6a3ff6764157dbdf1f50013471324dd352366f48805b0b37f232384b2b52ce2ee85d173468b62eaa052381a9588a317b3a1324d01a531a41fa7add6c5efbdd88f4718feed2bc0246be924e81bb90f03e49ceedf7af0dd48f06f265b519600bd082c6e6bd27eaa71cc0288df1ecc3b062b Prime1: 0xc5b471a88b025dd09d4bd7b61840f20d182d9b75bb7c11eb4bd78312209e3aee7ebfe632304db6df5e211d21af7fee79c5d45546bea3ccc7b744254f6f0b847f Prime2: 0xc20a99feeafe79767122409b693be75f15e1aef76d098ab12579624aec708e85e2c5dd62080c3a64363f2f45b0e96cb4aef8918ca333a326d3f6dc2c72b75361 Exponent1: 0x83cda11b0756e935be328fcebad5f6b36573bcf927a80bf2328facb6c0697c9eff2a9976cade79ea3ec0be1674fff4512e8d8e2f29c2888524d818df9f5d02ff Exponent2: 0x815c66a9f1fefba44b6c2b124627ef94b9411f4f9e065c7618fb96dc9da05f03ec83e8ec055d7c42ced4ca2e75f0f3231f5061086ccd176f37f9e81da1cf8ceb Coefficient: 0x10d954c9e2b8d11f4db1b233ef37ff0a3cecfffad89ba5d515449b007803f577e3bd7f0183ceddfd805466d62f767f3f5a5731a73875d30186520f1753a7e325
RSA keys for gateway mail -mail-keys:
[root@mail /]# cd / [root@mail /]# vi mail-keys
# 1024 bits, Fri Feb 4 04:46:59 2000 # for signatures only, UNSAFE FOR ENCRYPTION #pubkey=0x01037631b81f00d5e6f888c542d44dbb784cd3646f084ed96f942d341c7c4686cbd405b805dc728f8697475f11e8b1dd797550153a3f0d4ff0f2b274b70a2ebc88f073748d1c1c8821dc6be6a2f0064f3be7f8e4549f8ab9af64944f829b014788dd202cf7d2e320cab666f5e7a197e64efe0bfee94e92ce4dad82d5230c57b89edf Modulus: 0x7631b81f00d5e6f888c542d44dbb784cd3646f084ed96f942d341c7c4686cbd405b805dc728f8697475f11e8b1dd797550153a3f0d4ff0f2b274b70a2ebc88f073748d1c1c8821dc6be6a2f0064f3be7f8e4549f8ab9af64944f829b014788dd202cf7d2e320cab666f5e7a197e64efe0bfee94e92ce4dad82d5230c57b89edf PublicExponent: 0x03 # everything after this point is secret PrivateExponent: 0x4ecbd014ab3944a5b08381e2de7cfadde242f4b03490f50d737812fd8459dd3803d003e84c5faf0f84ea0bf07693a64e35637c2a08dff5f721a324b1747db09f62c871d5e11711251b845ae76753d4ef967c494b0def4f5d0762f65da603bc04c41b4c6cab4c413a72c633b608267ae2889c162a3d5bc07ee083b1c6e038400b Prime1: 0xc7f7cc8feaaac65039c39333b878bffd8f95b0dc22995c553402a5b287f341012253e9f25b83983c936f6ca512926bebee3d5403bf9f4557206c6bbfd9aac899 Prime2: 0x975015cb603ac1d488dc876132d8bc83079435d2d3395c03d5386b5c004eadd4d7b01b3d86aad0a2275d2d6b791a2abe50d7740b7725679811a32ca22db97637 Exponent1: 0x854fddb5471c84357bd7b777d0507ffe5fb92092c1bb92e37801c3cc5aa22b5616e29bf6e7ad1028624a486e0c619d47f428e2ad2a6a2e3a159d9d2a911c85bb Exponent2: 0x64e00e87957c81385b3daf9621e5d302050d7937377b92ad38d04792aadf1e8de52012290471e06c1a3e1e47a61171d435e4f807a4c39a6561177316c9264ecf Coefficient: 0x6f087591becddc210c2ee0480e30beeb25615a3615203cd3cef65e5a1d476fd9602ca0ef10d9b858edb22db42c975fb71883a470b43433a7be57df7ace4a0a3fExtract and copy the public RSA key files of deep and mail to your ipsec.conf files as shown below. You can locate the line related to the public key by a sentence beginning with the commented-out: #pubkey= line.
# sample connection conn deep-mail left=208.164.186.1 leftsubnet=192.168.1.0/24 leftnexthop=205.151.222.250 right=208.164.186.2 rightsubnet=192.168.1.0/24 rightnexthop=205.151.222.251 keyingtries=0 auth=ah authby=rsasig leftrsasigkey=0x010395daee1be05f3038ae529ef2668afd79f5ff1b16203c9ceaef801cea9cb74bcfb51a6ecc08890d3eb4b5470c0fc35465c8ba2ce9d1145ff07b5427e04cf4a38ef98a7f29edcb4d7689f2da7a69199e4318b4c8d0ea25d33e4f084186a2a54f4b4cec12cca1a5deac3b19d561c16a76bab772888f1fd71aa08f08502a141b611f rightrsasigkey=0x01037631b81f00d5e6f888c542d44dbb784cd3646f084ed96f942d341c7c4686cbd405b805dc728f8697475f11e8b1dd797550153a3f0d4ff0f2b274b70a2ebc88f073748d1c1c8821dc6be6a2f0064f3be7f8e4549f8ab9af64944f829b014788dd202cf7d2e320cab666f5e7a197e64efe0bfee94e92ce4dad82d5230c57b89edf auto=start
 :
Don't forget that, in this example,
:
Don't forget that, in this example,
The leftrsasigkey= parameter contains the public key of deep
The rightrsasigkey= parameter contains the public key of mail.
Modify your /etc/ipsec.secrets files to use RSA private keys in *each* gateway: Edit your original ipsec.secrets file, vi /etc/ipsec.secrets and add the RSA private key for authentication on both gateways: The ipsec.secrets file for gateway deep:
[root@deep] /# vi /etc/ipsec.secrets
You must change your original ipsec.secrets file as shown above to look like the following on both gateways. It is important to note that the private keys are not the same on both gateways, deep and mail. The private key for deep comes from the RSA key file deep-keys, while the private key for mail comes from the RSA key file mail-keys:208.164.186.1 208.164.186.2 "0x9748cc31_2e99194f_d230589b_cd846b57_dc070b01_74b66f34_19c40a1a_804906ed"
208.164.186.1 208.164.186.2: RSA { Modulus: 0x95daee1be05f3038ae529ef2668afd79f5ff1b16203c9ceaef801cea9cb74bcfb51a6ecc08890d3eb4b5470c0fc35465c8ba2ce9d1145ff07b5427e04cf4a38ef98a7f29edcb4d7689f2da7a69199e4318b4c8d0ea25d33e4f084186a2a54f4b4cec12cca1a5deac3b19d561c16a76bab772888f1fd71aa08f08502a141b611f PublicExponent: 0x03 # everything after this point is secret PrivateExponent: 0x63e74967eaea2025c98c69f6ef0753a6a3ff6764157dbdf1f50013471324dd352366f48805b0b37f232384b2b52ce2ee85d173468b62eaa052381a9588a317b3a1324d01a531a41fa7add6c5efbdd88f4718feed2bc0246be924e81bb90f03e49ceedf7af0dd48f06f265b519600bd082c6e6bd27eaa71cc0288df1ecc3b062b Prime1: 0xc5b471a88b025dd09d4bd7b61840f20d182d9b75bb7c11eb4bd78312209e3aee7ebfe632304db6df5e211d21af7fee79c5d45546bea3ccc7b744254f6f0b847f Prime2: 0xc20a99feeafe79767122409b693be75f15e1aef76d098ab12579624aec708e85e2c5dd62080c3a64363f2f45b0e96cb4aef8918ca333a326d3f6dc2c72b75361 Exponent1: 0x83cda11b0756e935be328fcebad5f6b36573bcf927a80bf2328facb6c0697c9eff2a9976cade79ea3ec0be1674fff4512e8d8e2f29c2888524d818df9f5d02ff Exponent2: 0x815c66a9f1fefba44b6c2b124627ef94b9411f4f9e065c7618fb96dc9da05f03ec83e8ec055d7c42ced4ca2e75f0f3231f5061086ccd176f37f9e81da1cf8ceb Coefficient: 0x10d954c9e2b8d11f4db1b233ef37ff0a3cecfffad89ba5d515449b007803f577e3bd7f0183ceddfd805466d62f767f3f5a5731a73875d30186520f1753a7e325 }The ipsec.secrets file for gateway mail:
[root@mail ]/# vi /etc/ipsec.secrets
Authentication by RSA Signatures requires that each host have its own private key. The key part of an entry may start with a token indicating the kind of key. RSA signifies RSA private key and PSK -which is the default signifies PreShared Key. Since PSK is the default, we must specify RSA, so that we'll be able to use RSA private keys in this file ipsec.secrets. The super-user root should own the file ipsec.secrets, and its permissions should be set to block all access by others.208.164.186.1 208.164.186.2: RSA { Modulus: 0x95daee1be05f3038ae529ef2668afd79f5ff1b16203c9ceaef801cea9cb74bcfb51a6ecc08890d3eb4b5470c0fc35465c8ba2ce9d1145ff07b5427e04cf4a38ef98a7f29edcb4d7689f2da7a69199e4318b4c8d0ea25d33e4f084186a2a54f4b4cec12cca1a5deac3b19d561c16a76bab772888f1fd71aa08f08502a141b611f PublicExponent: 0x03 # everything after this point is secret PrivateExponent: 0x63e74967eaea2025c98c69f6ef0753a6a3ff6764157dbdf1f50013471324dd352366f48805b0b37f232384b2b52ce2ee85d173468b62eaa052381a9588a317b3a1324d01a531a41fa7add6c5efbdd88f4718feed2bc0246be924e81bb90f03e49ceedf7af0dd48f06f265b519600bd082c6e6bd27eaa71cc0288df1ecc3b062b Prime1: 0xc5b471a88b025dd09d4bd7b61840f20d182d9b75bb7c11eb4bd78312209e3aee7ebfe632304db6df5e211d21af7fee79c5d45546bea3ccc7b744254f6f0b847f Prime2: 0xc20a99feeafe79767122409b693be75f15e1aef76d098ab12579624aec708e85e2c5dd62080c3a64363f2f45b0e96cb4aef8918ca333a326d3f6dc2c72b75361 Exponent1: 0x83cda11b0756e935be328fcebad5f6b36573bcf927a80bf2328facb6c0697c9eff2a9976cade79ea3ec0be1674fff4512e8d8e2f29c2888524d818df9f5d02ff Exponent2: 0x815c66a9f1fefba44b6c2b124627ef94b9411f4f9e065c7618fb96dc9da05f03ec83e8ec055d7c42ced4ca2e75f0f3231f5061086ccd176f37f9e81da1cf8ceb Coefficient: 0x10d954c9e2b8d11f4db1b233ef37ff0a3cecfffad89ba5d515449b007803f577e3bd7f0183ceddfd805466d62f767f3f5a5731a73875d30186520f1753a7e325 }